A cart abandonment rate is one of the biggest challenges of e-commerce. Every year e-commerce brands record losses estimated at US$18 billion with cart abandonment.1* Latin America, including countries in South and Central America, have a 75.3% cart abandonment rate.2* One of the most significant reasons for these abandonments is the friction perceived by the user during their act of purchase. Technology providers are working to reduce this friction by implementing Risk Based Authentication (RBA) algorithms in their solutions so that users (cardholders) are automatically authenticated, thus providing security for the entire electronic payments ecosystem.
1* CreditDonkey, Dynamic Yield.
2* CreditDonkey, 2022.
What is Risk Based Authentication (RBA)?
Risk Based Authentication, also known by the acronym of its initials RBA, is not an exclusive term for authentication in electronic transactions, but its application makes perfect sense for this purpose. This is a general term used to identify any authentication process that has its validation rules linked to a risk analysis based on the data provided for this purpose.
Bringing this concept to the universe of electronic transactions, the application of RBA happens in conjunction with a 3DS Access Control Server (ACS), recommending or taking actions based on the data obtained by the 3DS Methods protocol. This is supported by an EMVCo, referring to the 2 possible flows of customer authentication (cardholder) in an electronic transaction:
- Authentication without challenge: Risk analysis identifies low risk and recommends authentication without the cardholder needing to interact with the ACS.
- Authentication with challenge: the risk analysis identifies a medium or high risk and recommends an authentication in which the cardholder needs to interact with ACS, for example, enter a password sent by SMS.
How Does It Work?
In this application of the RBA being applied integrated to the ACS, the result of the risk analysis returns one of the two recommendations already mentioned above based on some of the following transaction information extracted from the 3DS protocol authentication request message:
- Customer Data
- Card Information
- Purchase Information
- Store Information
All this information is sensitive and therefore services related to financial transactions are developed and operated according to the strictest standards, as well as information security and are governed by governance instruments with annual audits of bodies such as Payment Card Industry (PCI), EMVCo and the brands themselves.
Unchallenged Flow
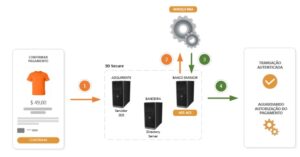
- When the customer confirms Checkout, the purchase and customer data passes through the 3DS protocol domains and is processed as an authentication request message until it reaches the Issuing Bank’s Access Control Server (ACS).
- The ACS consults the risk analysis service that processes the authentication request information.
- The risk analysis service validates the data by not finding inconsistencies in the transaction authentication request message against the defined rules/parameters, then informs the ACS that the transaction can be authenticated without customer interaction.
- ACS authenticates the transaction and then the payment follows the normal authorization flow.
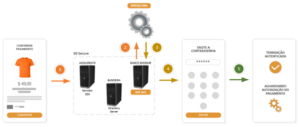
- Same flow process without challenge.
- Same flow process without challenge
- The risk analysis service finds some inconsistency in the data of the transaction authentication request message in relation to the defined rules/parameters, then informs the ACS that the transaction will be authenticated after successful customer interaction.
- The ACS presents the challenge screen, where the customer must enter the password received by SMS, email or other method of sending.
- After successful validation of the password, the payment follows the normal flow of authorization.
Benefits
One of the main challenges in an electronic transaction is the conversion rate, which is the rate related to the customer (card owner) who visits the page and even adds the item to the cart, but does not complete the purchase. And one of the biggest offenders for this practice is the friction at checkout, where the customer ends up giving up the purchase by having to perform additional authentication or verification steps. By integrating RBA into the ACS solution, the authentication process gains an important automation to assist the Issuing Bank in its decision making to challenge or not a transaction based on customer information, purchase information, behavioral aspects, device information used, and other data obtained from the 3DS protocol. Thus, for consumers who usually follow patterns in their e-commerce purchasing activities, RBA will tend to suggest the flow without challenge, thus decreasing friction in the authentication process safely for all participants in the process.
HST – Risk Based Authentication (RBA): more security for electronic transactions
Risk Analyzer is HST’s Risk-Based Authentication solution, operating in conjunction with HST-ACS 2.0 brings card-issuing banks more security and agility in the decision-making process regarding transaction authentication.
Want to know more about our solutions? Get in touch with our sales team!



Leave a Comment